Perimeter Intrusion Detection Systems (PIDS)
Bandweaver utilises Perimeter Intrusion Detection Systems (PIDS) to ensure that organisations are fully secure and to help reduce operational risk.
With ever increasing threat levels it is important that organisations properly secure their assets. This starts at the perimeter of their sites where there has never been a more important time to deploy robust, reliable and secure detection strategies to mitigate operational risk.
Prompt and highly accurate location information of a would-be intruder ensures a fast and appropriate response to minimise any loss. Ensuring that your perimeter intrusion detection system is fully integrated into your security solution provides real time data. Therefore creating the ability to track and respond to intruders.
Fiber optic technology is fast becoming the technology of choice. Especially for those organisations looking to deploy a cost-effective reliable solution with significantly lower full life cost of ownership.
Bandweaver’s advanced range of fiber optic intrusion detection solutions provide both covert buried and fence or wall mounted detection capabilities from a single detection unit. With fully scalable systems for sites less than 5km to more than 100km Bandweaver has the solution for you.
Intelligent Insights
Resistance to Cable Cut & Sabotage
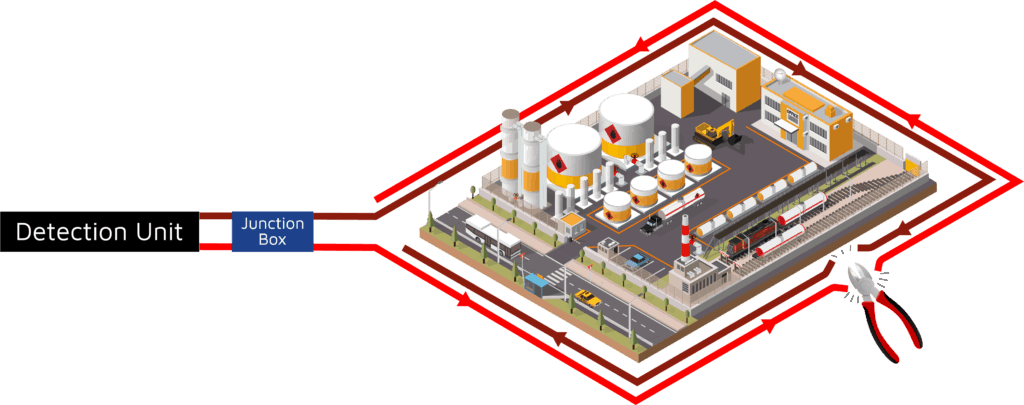
All Bandweaver PIDS detection units are offered in a 1 or 2-channel variant. The 2-channel variant will continue to provide uninterrupted detection along the perimeter. This remains true even if the cable is cut or damaged.
Minimising Nuisance Alarms
Using AI technology, our market leading detection algorithms are able to develop an acoustic fingerprint of different events. This enables the distinction between genuine security risks and extraneous environmental noise.
Location Accuracy
Advanced signal processing technology combined with intelligent algorithms enables fast and accurate identification of the specific location of a potential threat to within ±5m.
Integration
Our advanced software is capable of seamless integration with a wide variety of commonly used 3rd party systems. This provides operational teams with real-time information from a range of devices via a single interface.
Lower Cost of Ownership
Overall reduced cost of installation and maintenance when compared with alternative technologies. Additionally, no power is needed in the field.
Multiple Fence Types
Due to its unique configuration capabilities, the Bandweaver solution is suitable for every fence type without compromising location accuracy or event classification capability.
Covert Buried detection
Our buried solution is totally covert and can detect personnel and vehicles long before they gain access to a site and is ideal where there is a lack of physical delineation
Advanced Fiber Optic Sensing Solutions: Security
Fence mounted intrusion detection
Bandweaver optical fiber detection is suitable for all fence types including chain link, weld mesh, and palisade. With advanced event classification the system can detect multiple simultaneous intrusion attempts with location accuracy down to ±5m.
Fence climbing, cutting and lifting are all detected with a probability of detection (POD) greater than 95%. Alongside this, the intelligent processing ensures that there are minimal nuisance alarms.
There is no requirement for power in the field and optical fiber cabling is unaffected by electromagnetic interference. The cabling itself is intrinsically safe so is suitable for sites that are at risk from fire or explosion.

Wall Mounted Intrusion Detection
Bandweaver’s optical fiber detection is suitable for wall mounting and will detect intruders climbing over or attempting to break through a wall. This makes it suitable for both perimeter and building walls.
Optical fiber cable can also be deployed on wall toppers such as barbed or razor wire to ensure full site detection capability. Our advanced signal processing minimises nuisance alarms caused by environmental background noise.
Covert Buried Intrusion Detection
Direct buried optical fiber cable can be deployed to protect perimeters where there is no physical delineation. With the ability to detect intruders before they enter site whilst remaining covert buried detection has a number of significant advantages over other technologies.
With the ability to distinguish between multiple intruders and vehicles the buried intrusion detection solution is a fast to deploy, low cost but highly resilient solution and is suitable for all soil types, it is especially suitable for protecting extended borders.
The Four Main Types Of Perimeter Intrusion Detection Systems
There are four main types of Perimeter Intrusion Detection Systems, these are:
Barrier-Mounted – Fence Intrusion Detection System
PIDS deployed on or in conjunction with a fence or other physical barrier (e.g. DAS cable or other motion sensors mounted on a fence).
Ground-based or Below-ground
PIDS deployed below ground (again a DAS cable can be used or pressure sensitive cable or electromagnetic field). These do not require a physical barrier.
Free-Standing
PIDS deployed above ground that do not need to be installed on or in conjunction with a physical barrier (e.g. bistatic microwave link).
Rapidly Deployable
PIDS that are designed for temporary deployment; for example, to protect a mobile asset. Typically this would cover military applications and again DAS sensing technology has been very successfully deployed in these environments.
Solutions Selection Guide
When deciding on the specification and selection of any Perimeter Intrusion Detection Systems the following factors must be taken into consideration:
- Landscape, flora, fauna and topographical features
- Integration with other types of equipment or systems
- Climatic conditions
- Local regulations
- Presence (or lack of) physical barrier and robustness against threats
- Duration of required deployment (rapidly deployable PIDS)
- Response force arrangements
- Personnel on site
All of these factors will affect the key choices made by an organisation and there are also other-point to consider including:
- Whether a line of site technology is appropriate (e.g. radio wave based technology or camera based systems). For instance, are there any undulations in the ground surface? Undulations occurring over the distance of a metre andup to several tens of metres can shield the presence of an intruder from some detection technologies, particularly in the case of microwave systems, visual cameras andactive or passive infrared.
- Does the detection system needs to be covert (buried or hidden)?
- Are there specific electromagnetic interference issues that will affect specific technologies or are there requirements for the technology to be intrinsically safe (e.g on oil rigs or process plants)?
- Is there existing infrastructure to mount the system or whether it will be part of a new build?
- How does the system integrate with the overall security strategy.?What constitutes an alarm and what action is taken in the event of an alarm (audio alarm, visual alarm or a combination)?
In some scenarios, particularly where perimeters are large or the asset is critical, the asset owner may choose to use multiple technologies and integrate the respective monitoring systems through a centralized control system (e.g. Video cameras combined with DAS, where the cameras slew to the specific event when an alert is raised.)
Perimeter Intrusion Threat Types
As mentioned above DAS systems are able to classify events according to their acoustic signatures. Typically the types of classifications that are required in most intrusion scenarios include:
Personnel movement
The systems can detect personnel walking and monitor the cadence of the footfall, enabling the distinction between walking and running and also to distinguish between bipeds (people) and quadrupeds (animals). Typically for walking this can be alerted within 5 m of the cable.
Vehicle movement
Vehicles will be detected both from the sound of the engine and the energy dissipated in the ground. Depending on the size of the vehicle these can be detected within 10-20m from the cable.
Digging or drilling
Digging whether it is a person or a mechanical machine imparts rhythmic and high energy bursts into the ground and has a clear signature. The typical range is from 5-50m depending on how large the mechanical vehicle.
Distributed Acoustic Sensing for Security
Distributed Acoustic Sensing systems can monitor the acoustic signals along the length of the fiber optic cable and are able to classify the acoustic signatures and pinpoint the location of an intrusion event to typically within 5 m.
The distributed acoustic sensing system consists of an interrogation unit with the relevant optoelectronic components (laser source(s), detectors and associated processing hardware, firmware and software) to monitor a length of optical fiber cable which can be run outside, on and inside the perimeter. These DAS systems have different distance capabilities ranging from 5 km to 100 km. The examples below show how a single system can be configured to monitor inside, outside and on the perimeter itself.
The fact that the systems are able to classify the event and to provide an “acoustic fingerprint” of the intrusion event is very powerful as this allows the system to distinguish between personnel, vehicles, animals and whether specific activity is occurring (such as digging or fence climbing).
Whether the cable is buried or fence or wall mounted will affect how the system is tuned and used. For a buried cable a lot of the high frequency noise is filtered out by the earth surrounding the cable and so it is less susceptible to false alarms caused by environmental events.
Bandweaver Products for Perimeter Protection
Robustness of System
Response to Multiple Alarms
Multiple alarms may be a deliberate diversion caused by a potential intruder. Consideration should be given, therefore, to how multiple alarms will be stacked or queued by the entire system, or for an individual zone, and whether alarms from particular zones should be given higher priority.
DAS systems have the ability to configure multiple smart zones, with user configurable alarms for each zone which can be adapted as the environmental conditions evolve in order to prevent nuisance alarms from such events. They can also detect multiple events at once and so this makes it more challenging for the intruder to attempt diversionary tactics.
Cut Resilience
Fiber optic cable perimeter intrusion detection offers a simple to install solution that has no requirements for power in the field which reduces the over all cost of ownership. With fan free technology, no moving parts and utilising high reliability telecoms components this equates to high percentage uptime ensuring years of reliable detection capability. With a location accuracy of intrusion events to ±5m it enables the ability to rapidly react to any perceived threat.
Full System Integration
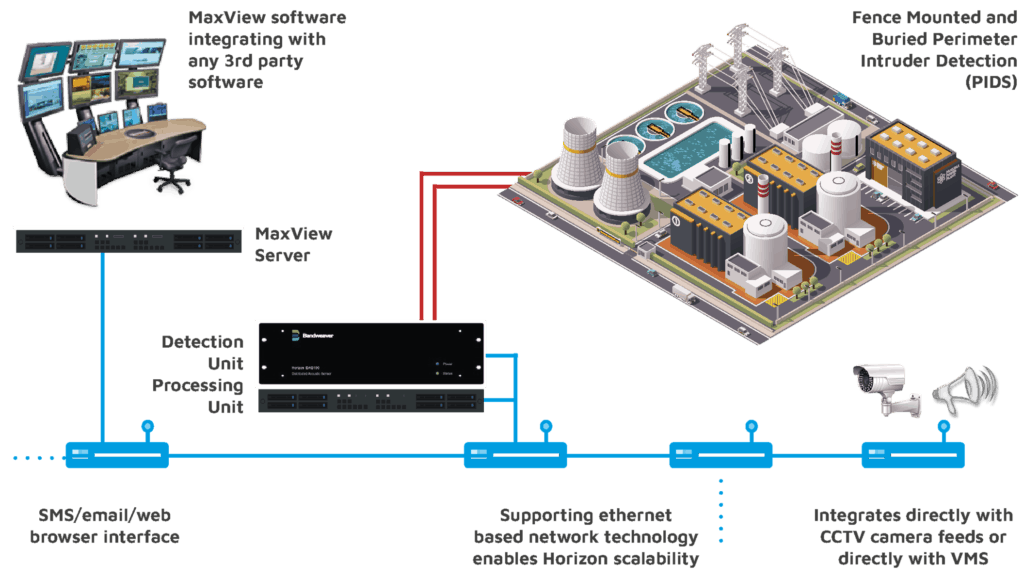
System Architecture
Bandweaver’s detection units have extremely flexible system architecture enabling multiple units to be networked together and integrated with Bandweaver’s MaxView software or any 3rd party security management system.
With the loose coupling architecture of Bandweaver’s MaxView it can integrate multiple systems across multiple sites with one coherent, customisable, easy to install user friendly interface.
MaxView Software
MaxView’s flexible architecture provides a complete solution which allows operators to integrate numerous subsystems across multiple sites ensuring a fast and appropriate response to an intrusion event.
MaxView Key Functions:
Powerful Visualisation – MaxView’s easily configurable interface allows the user to design the user interfaces according to their operation’s specific needs. Visualisation includes options such as 2D GIS mapping, bespoke schematic diagrams, overlay on site photo’s/diagrams or interactive 3D modelling.
Data Management and Consolidation – MaxView’s loose coupling architecture allows import data streams and feeds (3rd party sensors, CCTV, fire and intrusion alarm systems, access control, video feeds, etc) from multiple sites into one coherent centralised system.
Data Export to PSIM, VMS systems, SMS, etc – MaxView can output data to a wide variety of control systems. As standard MaxView can manage all of the most common standard communications protocols.
Click here to view the MaxView for security brochure.